Computer Networks
Malware Traffic Detection and Malware Experimentation Design
By Berkay Celik, PhD
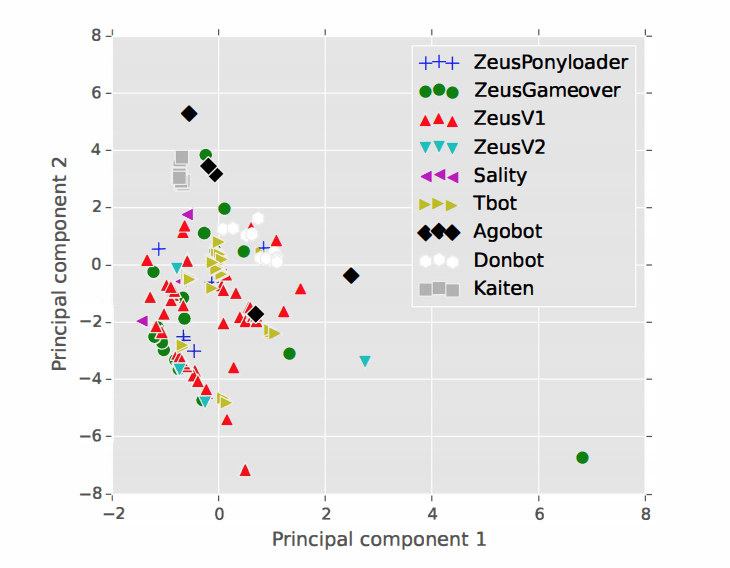
In this project, we present a framework for evaluating the transport layer feature space of malware heartbeat traffic. We use these features in a prototype detection system to distinguish malware traffic from traffic generated by legitimate applications. Further, we characterize the evolution of malware evasion techniques over time by examining the behavior of 16 malware families. In particular, we highlight the difficulty of detecting malware that use traffic-shaping techniques to mimic legitimate traffic. We also take a closer look at the experimentation artifacts of malware detection. For instance, we find that current approaches do not consider timing-based calibration of the malware traffic traces prior to using this traffic to salt a background enterprise traffic trace. We found that timing-based features of the malware traffic may be artificially distinctive, potentially leading to (unrealistically) optimistic classification results.
This project lead to three papers: Malware Traffic Detection using Tamper Resistant Features (published in IEEE MILCOM 2015), Salting Public Traces with Attack Traffic to Test Flow Classifiers (published in USENIX CSET 2011) and Malware Modeling and Experimentation through Parameterized Behavior (published in JDMS 2015).