Internet of Things (IoT)
Automated IoT, Safety and Privacy Analysis
By Berkay Celik, PhD
In this project, we implemented two systems and a toolset to analyze IoT applications: Soteria, Saint and IoTBench.
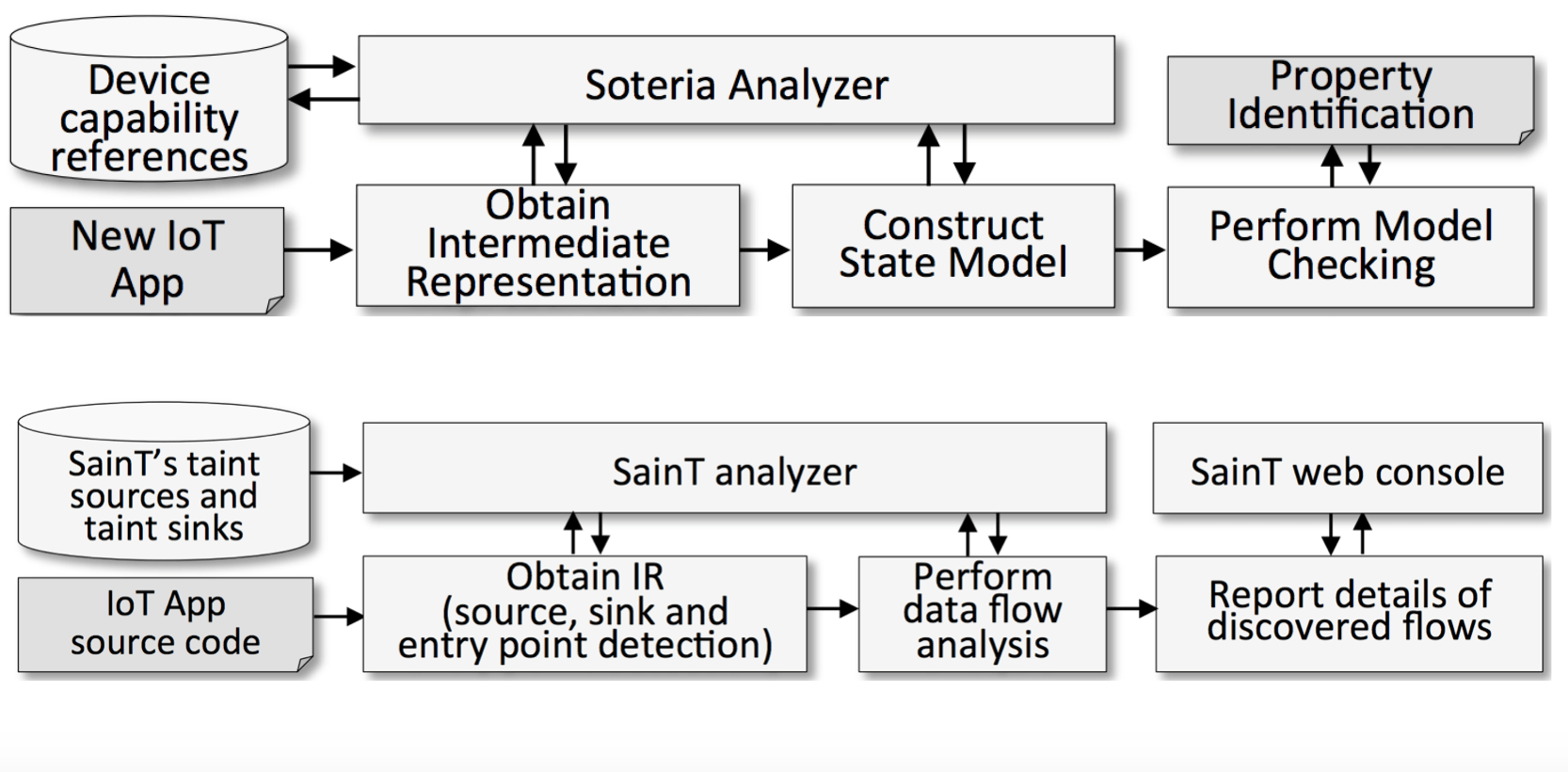
Soteria is a static analysis system for validating whether an IoT app or IoT environment (collection of apps working in concert) adheres to identified safety, security, and functional properties. We demonstrated that many apps violate properties when used in isolation and when used together in multi-app environments. This work was presented in USENIX ATC 2018.
Saint, a static taint analysis tool for IoT applications. Through this effort, we introduced a rigorously grounded framework for evaluating the use of sensitive information in IoT apps–and therein provide developers, markets, and consumers a means of identifying potential threats to security and privacy. This work was presented in USENIX Security 2018.
IoTBench is an IoT-specific test corpus, an open repository for evaluating systems designed for IoT app analyses. IoTBench is under continual development, always welcoming contributions of the new IoT apps. The code for IoTBench is available here.
Detection under Privileged Information
By Berkay Celik, PhD
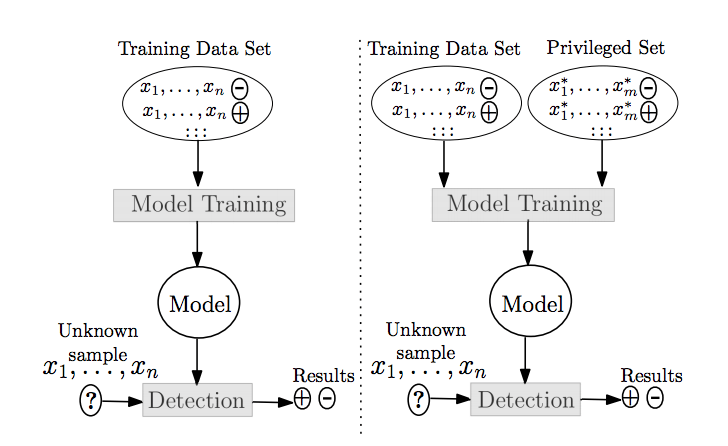
Training of machine learning models has been historically limited to only those features available at runtime. In this study, we ask “How can detection systems integrate intelligence relevant to an attack that is available at training time, yet not available at runtime?”. Consider a rootkit detection system for mobile phones. Obtaining a set of features may drain the battery even though they contribute to the detection of a rootkit. Therefore, the users might disable the system because the battery dies very quickly. However, obtaining these features at training time is feasible as we have unlimited resources in a laboratory-based environment. We built an alternate model construction approach that trains models using privileged information–features available at training time but not at runtime, yet samples are classified without the need of privileged features at runtime. Turning to the rootkit example, the features draining the battery are the privileged features.
This paper was accepted to AsiaCCS’18: Detection under Privileged Information. Read more about formulation and implementation in our technical report, and Feature Cultivation in Privileged Information-augmented Detection.