Exploring the OWASP Top 10: Part 2
One of the top ten security risks identified by OWASP is identification and authentication failures., which they discuss in this report: https://owasp.org/Top10/A07_2021-Identification_and_Authentication_Failures/. This is a big risk because it allows unapproved individuals to gain access to peoples accounts and systems and, as a result, sometimes elevated permissions or access to private information.
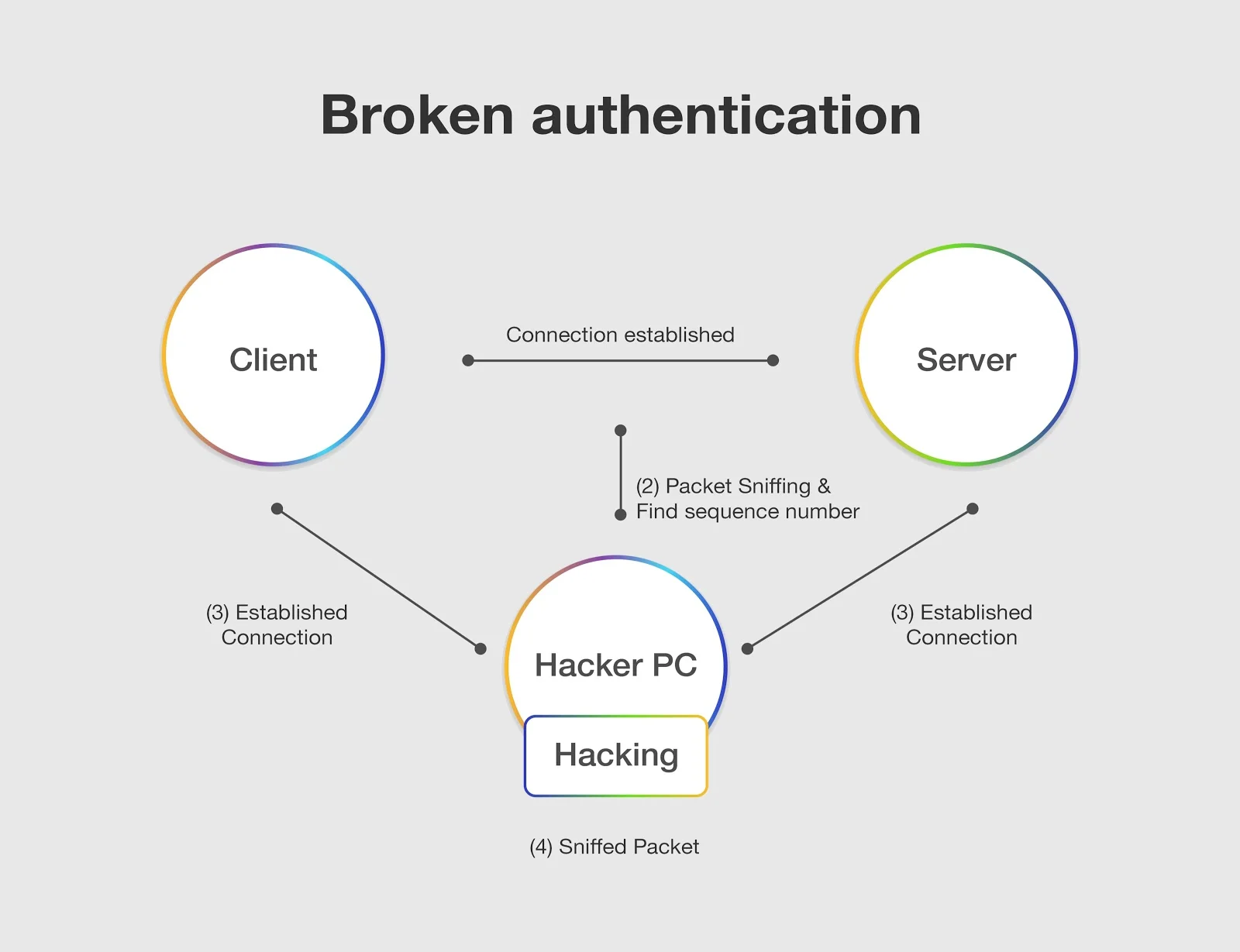
Confirmation of the user’s identity, authentication, and session management is critical to protect against authentication-related attacks. There may be authentication weaknesses if the application permits automated attacks such as credential stuffing, where the attacker has a list of valid usernames and passwords, permits brute force or other automated attacks, permits default, weak, or well-known passwords, uses weak or ineffective credential recovery processes, uses plain text, encrypted, or weakly hashed passwords data stores, neglects to use multi factor authentication, does not correctly invalidate session IDs, or exposes the session identifier in the url.
These vulnerabilities can make way for multiple different attacks. Credential stuffing, which is making use of a list of known passwords, is a common attack. If an application does not implement automated threat or credential stuffing protection, such as delaying the amount of login attempts someone could make, credential stuffing is an easy way for a hacker to gain access to someone’s account or system. Another big issue is using a public computer or system. If session timeouts aren’t properly set and someone forgets to log out when they finish using it, the next person to use it would have access to their account. Cyolo goes into a lot more detail about the different types of attacks that can result from this: https://cyolo.io/blog/identification-and-authentication-failures-and-how-to-prevent-them/.
There are a few things someone can do to combat this. Where possible, implement multi-factor authentication to prevent automated credential stuffing, brute force, or stolen credential attacks. Applications can implement weak password checks and require a certain amount of characters and numbers in passwords. Application developers can also ensure that registration, credential recovery, and API pathways are hardened against account enumeration attacks. One can limit or increasingly delay failed login attempts. To prevent incorrectly invalidating or exposing a session ID, applications may use a server-side, built-in session manager that generates a new random session ID with high entropy after login. Veracode talks a lot more about how to prevent these risks in their guide: https://info.veracode.com/rs/790-ZKW-291/images/identification-authentication-failure-prevention-guide-en.pdf.