Exploring the OWASP Top 10: Part 4
One of the top ten security risks identified by OWASP is broken access control according to their report https://owasp.org/Top10/A01_2021-Broken_Access_Control/. Access control enforces a policy so that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user’s limits. This picture is a brief explanation on how an attacker gains access:
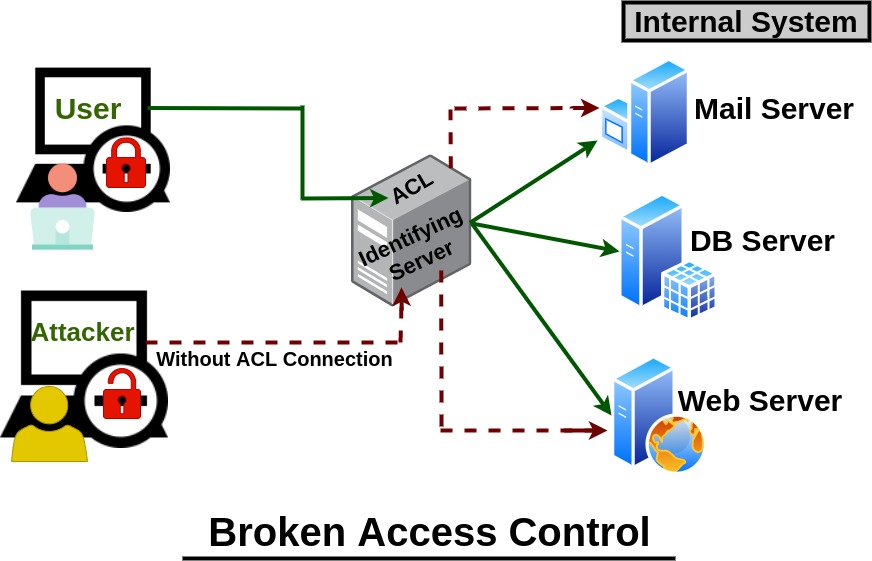
Red Hat gives some good information about access control and explains three different types in their article: https://www.bing.com/search?q=broken+access+control&cvid=59f8de25013e483a9898f791fe6e051a&gs_lcrp=EgZjaHJvbWUqBAgAEAAyBAgAEAAyBAgBEAAyBAgCEAAyBAgDEAAyBAgEEAAyBAgFEAAyBAgGEAAyBAgHEAAyBAgIEADSAQgzMDExajBqNKgCALACAA&FORM=ANAB01&PC=LCTS
Common access control vulnerabilities include failure to utilize the least privilege practice or deny by default practice, where access should only be granted for specific capabilities, roles, or users, but is available to anyone. Another common issue is bypassing access control checks by modifying the, internal application state, or the HTML page. Allowing the ability to view or edit someone else’s account is another bad practice that can lead to attacks. Elevation of privilege is a common method attackers use to gain more permissions on a system. This comes in the form of acting as a user without being logged in or acting as an admin when logged in as a user. Another mistake is force browsing to authenticated pages as an unauthenticated user or to privileged pages as a standard user.
Access control is only effective in trusted server-side code or server-less API, where the attacker cannot modify the access control check or metadata. There are multiple ways to avoid these issues. Except for public resources, use the deny by default method when granting permissions. Implement access control mechanisms once and re-use them throughout the application. Ensure that model access controls enforce record ownership rather than accepting that the user create, read, update, or delete any record. Applications should disable web server directory listing and ensure file metadata and backup files are not present within web roots. Be sure to log access control failures, alert admins when appropriate. Session identifiers should be invalidated on the server after logout. Veracode explains some other ways to prevent broken access control: https://info.veracode.com/rs/790-ZKW-291/images/broken-access-control-prevention-guide-en.pdf.