I’ve learned through researching digital privacy that people unintentionally leave behind evidence of their online activity. Images with metadata, such as location or authorship, are stored in formats like EXIF.
The reality of data mining defies the idea of online anonymity. Methods such as data mining examine locations, facial features, language usage, and other aspects to match and identify distinct individuals.
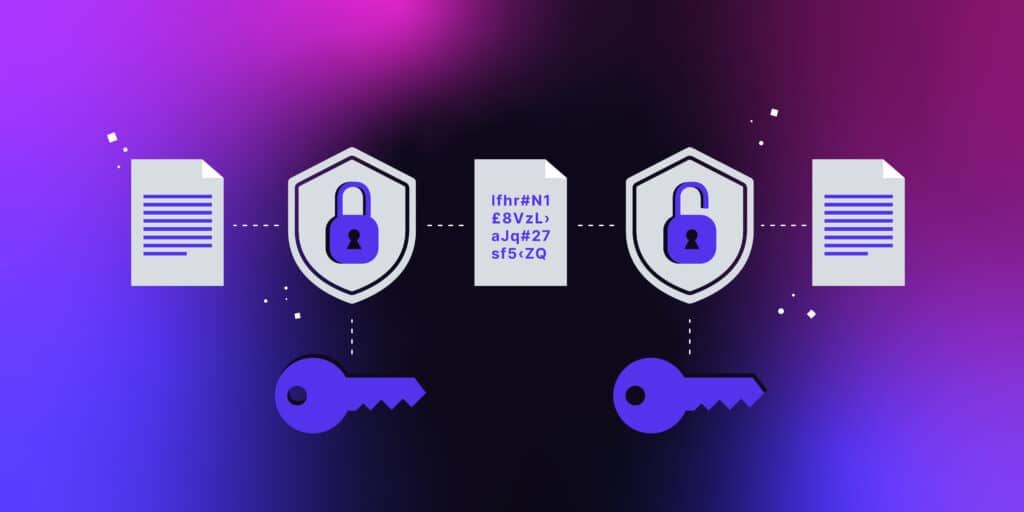
The necessity of encryption is highlighted by the possibility of eavesdropping. By converting plaintext into ciphertext, encryption acts as a barrier to prevent unwanted access. Cryptographic keys are used to perform encryption, which is a common feature of communication protocols.
Phishing is an emerging threat that involves unsuspecting users being tricked into believing they are legitimate entities through emails, with the goal of obtaining sensitive information. These insights underscore the need for vigilance in the digital landscape, emphasizing the importance of privacy-conscious practices.
Group Discussion :
I find that the dynamic relationship between privacy and database technology is complex and constantly changing. Privacy norms are being impacted by cultural shifts, especially among younger generations who are used to sharing on social media, and advanced databases are adding complexity.
Acquisti and Grossman’s research highlights a propensity to ignore long-term privacy implications when making online purchases, which raises questions about the extensive storage and processing of personal data by powerful database systems.
Cases from the real world, such as the Cambridge Analytica affair, underscore the fine line that separates privacy invasion from personalized services. This highlights the dual nature of database technology, which increases productivity but raises issues with consent, security, and unanticipated consequences.
Imaginary situations, particularly regular access to private medical records for research purposes, raise moral questions about data ownership, consent, and potential discrimination based on personal health information.
Legal and ethical frameworks must change in tandem with database technologies in order to be navigated responsibly. The need to protect individuals’ right to privacy in the digital age is becoming increasingly apparent, as evidenced by laws such as the General Data Protection Regulation (GDPR).
Link to homework
https://sites.psu.edu/dara/files/2023/12/LO11.docx